Wednesday, December 31, 2008
New law will let govt snoop on your PC
With Parliament on Tuesday passing a bill which stipulates life imprisonment for those indulging in cyber terrorism and giving the government endless power to "intercept or monitor any information through any computer resource," experts fear that "unauthorised interceptions could soon become common".
Calling for setting up of an independent authority to review complaints of unauthorised interceptions, cyber law expert Pavan Duggal told TOI that the bill was bound to infringe on civil liberties like right to privacy or right to anonymous communication with legitimate purposes, because no safeguards had been put in place to prevent such abuse.
Calling the bill "a hurried reaction", Duggal said, "The potential for misuse of these powers stipulated by the bill for political gains can't be ruled out."
There also appears to be no effective remedy or mechanism to appeal against unauthorised interception, Duggal said. "Once it becomes law, the government will have sovereign and blanket power to intercept or peep into any electronic communication of even legitimate citizens. Because the bill states that safeguards would be stipulated at a later date, it would clamp down on civil liberties right away. While we are concerned about national security, we don't want these interception mechanisms to become a handle for misuse," he added.
"There has to be a proper balance between contradictory subjects of interception and privacy. So safeguards are critical," the expert said. The Information Technology (Amendment) Bill 2008 also empowers the government with absolute power to block websites in national interest.
The government's move to bring in new provisions to tackle cyber terrorism comes after repeated instances of terrorists using the web to propagate mayhem and claim responsibility after every act.
For those indulging in cyber terrorism, the new legislation provides for stiff penalty of life imprisonment. The bill also says that dishonestly receiving stolen computer resource, identity theft, cheating by personation by using computer resource and violation of privacy will result in imprisonment upto three years apart from fine between Rs 1 lakh to Rs 10 lakh.
Transmitting material containing sexually explicit acts in electronic form would be punishable by imprisonment of upto five years along with a fine of upto Rs 10 lakh.
Emphasising on the overriding power given to government, a senior IT official pointed out that Section 69 of the original Act had given the central government the power to intercept and monitor any information through computer systems
in national interest, permitting it to monitor any potentially cognisable offence.
ET
Sunday, December 14, 2008
Some more info about Com Saketh Rajan by Jothindra
Com Saketh Rajan on his blog .
While it is a long post.. I have only cross posted the relevant parts..
Dec 9th , 2008
jotindra.blog.co.in
Notes from Kodagu
Come summer season, I recollect nostalgically of my 2 years stay in Kodagu, the little district in Karnataka. I was in the Administrative Service then. And one of the joys of it was being able to explore the places all over the state. One of the most memorable stints of my career was undoubtedly the one at Kodagu. The job was not strenuous as it is a very small district. And there was plenty of time to walk around the place................................................
.............................................
I’m used to seeing peacocks and herds of deer, why even elephants and bisons on the roadside itself. But it’s not the case here. I passed ‘Anekadu’(literally, elephant forest) between Suntikoppa and Madikeri a hundred times and yet didn’t get to see a deer! Maybe that speaks of the hunting instinct of the Kodavas.
And looking at the thick, wet forest reminded me of my once dear friend Saketh Rajan. What made him decide to give up a comfortable life to a life in the jungles? Could he not have tried to change the society through journalism instead of becoming a naxalite? What a journalist he could have been! I came to know him during the debate competitions. He used to represent Yuvaraja’s College, Mysore, and I, alongwith one B.N.S. Reddy , used to represent the Maharaja’s College. We were fascinated by his debating skills. What language, what clarity, what presentation Saketh had! He realized that he had erred in joining a course in Science and then decided to join Maharaja’s College with journalism as one of his subjects.
Inspite of becoming our junior, we grew to be close friends. He was so humble, so simply clad that for a longtime, we wondered how he had mastered the English language so well. Only later did we come to know that he was the son of a retired Army officer and the owner of a petrol bunk. After we came out of the college, we lost touch with each other. Only occasionally did we meet. But we came to know that he had changed a lot after his year’s stint at the All India Institute of Mass Communication in Delhi. He probably got in touch with the naxalites there. Maybe he thought that waging a war through Press was inadequate and so must have also joined the movement. This time he could not backtrack from the mistake he committed for he was playing a very dangerous game now. He had to go underground.
The last time I saw him was near the Ashoka Circle in Mysore. I saw him pushing a cycle. Some villagers were with him. We spoke for just a few moments exchanging greetings and I realized how drastically he’d changed. He was no longer the Saketh we knew. The tale has an interesting twist. He was very close to B.N.S.Reddy and one Lingaraj Gandhi. The latter is a Professor in the University of Mysore now. And the former-a top ranking Police officer! What a filmy ending it would have been if he had been on the assignment which ended with Saketh being shot dead in the forests around Shimoga a few years ago. Surely, strange are the ways of God!
..............................................................................
.............................................................................
Related Posts
Shashikiran another friend of Com Saketh Rajan writes a blog post on him
A poem by Com Saketh Rajan on Ken Saro Wiwo
Tuesday, November 25, 2008
Maoists now popular in Tamil Nadu Colleges
Police were jolted awake when the probe into the shoot-out in Vadakaunji forests near Kodaikanal in April 2008 revealed that three of the eight who escaped were college students. A wanted extremist—Navin alias Prasad of Naickankottai in Dharmapuri district—was killed in that encounter. During further investigation, it was found that one of those absconding, Kathir, a student of a government college in Madurai, had not been attending classes since January 2008. The other two—Senthil and Meenakshi—are students of an aided college in the southern city.
All three come from a very poor background, which made them vulnerable to extremist thinking. Their parents had no idea about their activities. “They believed their wards were working for some voluntary organisations,” said a senior police official.
The Maoists had influenced scores of other students too. However, only three of them, after several layers of filtering, graduated to the level of undergoing weapons training. The official added, “Their base is quite big. We have identified more than 100 people, including many students, who were in the Maoist loop in Madurai region alone. This is the first case in which we have been able to establish direct links between Left extremists in the state and the CPI (Maoist) central committee. Mallaji Rao, a member of the central committee, who was arrested in Kerala recently, had visited Tamil Nadu camps too. So far, we had only suspicions about such links.”
Tamil Nadu is not yet on the red corridor map. Though there have been intermittent efforts by extremists to regroup with a view to creating compact revolutionary zones within the state—Uthankarai in Dharmapuri district in 2002, Murugamalai near Periyakulam in Theni district in July 2007 and Varshanadu in Theni district in December 2007—they were put down with an iron hand by the state police.
Still, the state is far from being a territory where Left extremism has failed. The Madurai module has come as a bolt from the blue for police. “Extremists have targeted Madurai for two reasons: It is an urban area where their activities will go unnoticed and more importantly, it has forests within reachable distance for organising arms training,” said an intelligence official.
TOI
This article has one thing wrong LDO's stand for Legal Democratic Organisations
and not local democratic organisations.
Edu institutions to be sensitised on Maoists
CHENNAI : The state home department has cautioned the school and college education departments on suspected Maoist activities in educational
institutions across Tamil Nadu.
Home secretary S Malathi told TOI, “We have already alerted the school and college education departments. We will follow it up with more sensitisation programmes. Schools and colleges will have to keep a tab on students who stay back after class hours and those who do not attend classes for long. Authorities will also have to maintain contacts with the parents and inform them about their wards’ behaviour.”
In view of several students coming under the influence of Maoists, state police are also working on an advisory to be circulated in all educational institutions.
There have been recent instances of Left extremists trying their luck in schools too. On November 21, four cadres of the Revolutionary Students’ Youth Front (RSYF) assaulted Thirunavukkarasu, headmaster of the government higher secondary school at Thittachery in Nagapattinam district, when he refused them permission to enlist students in their movement. They were later arrested and remanded.
Making the task of the monitoring agencies difficult, Left extremists in Tamil Nadu have floated close to 50 local democratic organisations (LDOs) in Madurai, Theni, Dindigul, Coimbatore, Dharmapuri and Krishnagiri districts. As these LDOs are independent entities, there is little coordination among them. Only the hard-core elements in these groups maintain contacts with the area and state-level committees of the CPI (Maoist). It is estimated that Tamil Nadu has roughly a dozen hard-core Maoists, who are still at large. “As of now, we do not have concrete evidence to link any of these front organisations with subversive activities and hence cannot ban them,” said a senior police official.
Tamil Nadu police have instituted Naxalite special divisions (NSDs) under the supervision of superintendents of police in Maoist-infested districts. In consultation with the Q branch of the state police, the government has also carried out socio-economic development programmes worth Rs 14 crore in Krishnagiri and Dharmapuri districts. The scheme is expected to be extended to other sensitive districts next year.
Also, police will take up the task of training forest personnel in intelligence gathering with special focus on CPI (Maoist) and its front organisations. Forest personnel form a vital link in the fight against Maoists because all over India, extremists have been using forests to consolidate their force.
The director general of police had a meeting with the principal chief conservator of forests two months ago to discuss the modalities of the training programme for forest personnel. The training is expected to start next month.
TOI
Sunday, November 23, 2008
Reflections on Revolutionary Violence
Reflections on Revolutionary Violence
In the last one year, I have often found myself going back to a conversation I had had with a Maoist ideologue. As it happened, it was he who started interrogating me about my stand on violence. ‘So, you have become a Gandhian?’ he demanded. I must confess I was a bit taken aback, not quite able to figure out the context of this poser. ‘What do you mean by Gandhian’, I kind of mumbled. Pat came his reply: ‘Well you have been making some noises lately about Maoist violence, haven’t you?’ Suddenly it all became clear. Through this ridicule, he was trying to appeal to that part of me that still remained marxist – presumably now buried in some remote past – and to resurrect it against my ostensible ‘non-marxist’, ‘liberal’ present (for which ‘Gandhian’ was some kind of a short hand code). I found myself at a loss of words. Does a criticism of the mindless and nihilistic violence of the Maoists make one a Gandhian? Is there no space left between these two polar positions? The conversation did not go very far that day but has kept coming back to me ever since.
I must hasten to add though that in this day and age, I do not find the epithet ‘Gandhian’ atrocious as I might have two decades ago. Notwithstanding Gandhi’s completely wrong-headed approach to the struggle against caste and on matters of class, there are aspects of Gandhi that make him appear far more visionary today than any other leader, thinker or political current of his time. But more on that some other time.
The reason I have been going back to that conversation quite often lately is that I have begun to feel this disappearance of the middle ground ever more intensely. You can either be one or the other – and this choice is forced on us equally by the state as by the ‘revolutionaries.’ The last one year has furnished more and more evidence of the fact that it is the state that wants us to make this impossible choice: either you with us or you are a Maoist. We have on earlier occasions, written on Kafila about how the state has been working overtime manufacturing Maoists – branding activists like Roma in Sonbhadra or elsewhere as Maoists, arresting the likes of Binayak Sen and keeping them under indefinite detention for being a ‘Maoist’. The state’s demand is indistinguishable from that of the Maoist ideologue - an unholy and unstated compact, if you will of dividing up the political space at least in some parts of India. And the fundamental premise underlying this demand, as always, is that ‘this is a war.’
This is war indeed. You can substitute ‘Islamic terrorist’ and ‘the Nation’ for the terms above and the argument will remain structurally identical. So, this is war – war on terror for the State and a war of liberation or jehad for the revolutionaries. And haven’t we learnt that ‘all is fair’ in war. It is the logic of ‘war’ that enables the State/Nation and its security forces to stage encounters, kill, arrest and torture innocents while suppressing any critical voice as anti-national. That is what enables the state to suspend the ordinary processes of law and promulgate / invoke extraordinary laws that negate every democratic norm. It is never the ‘revolutionary’ - Maoist or Islamic or any such - who is arrested and tortured. In this neat compact, we have the perfect elimination of all middle ground - everybody is a suspected Maoist or jehadi on the one hand or an anti-national terrorist on the other. If Mao wanted his guerrillas to live among the peasant masses like fish in water, his followers have successfully dried up the river. There ain’t no water. It is thus the purely military organization of terror that stalks these parts of the country. That is why the life of the common person in the tribal areas of Chhattisgarh shares so much with that of an ordinary urban Muslim today: always at the mercy of the one or the other.
To a revolutionary – it matters little whether s/he is spurred by the ideology of ‘Maoism’, nationalism or global radical Islam – all such talk is sentimental nonsense. All talk that mourns the loss of innocent lives is nonsense precisely because it privileges the small, local, everyday joys and sorrows over the large Utopias of Liberation. Utopias that are precisely that – U-topias or nonplaces. If one sifts through the debris of twentieth century political thought and practice, one will see that violence is intrinsic to the Utopian imagination, to the desire to build the world in its own image. Stalinist socialism, Hitlerite National-Socialism, the Maoist Cultural Revolution or Pol Pot’s racial Khmer ‘socialism’ – all share one characteristic: They wanted to mould the world according to their vision and produce a frightening, monochromatic uniformity. And not surprisingly all of them drew heavily on the military imagination: Red Armies, the Sturm Abteilung or the Freikorps, the spectacles of grand parades, a militarily regimented society and what have you…
Dig deep into that debris of nineteenth and twentieth century political thought: you will not find one enduring change that this frenzied search for ‘power’ has produced. These messianic utopian movements did succeed in capturing state power but all the change that they produced – if at all – was ephemeral, as short-lived as the revolutions themselves. Democracy, universal suffrage, eight-hour working day, the civil rights struggles, the struggles against gender and caste discrimination, the recognition of different sexualities – all these are transformations that have taken place without armed vanguard militias, as part of patient, everyday struggles.
Even capitalism has changed over the last century and a half because of workers struggles and the impact of ecological movements – not because armed revolutionaries ‘captured state power.’ In fact, the greatest irony is that the impact of the seizure of power on the nature of capitalism, if any, was not where power was captured but elsewhere – in the industrialized capitalist countries, in the form of the New Deal and the welfare state. Everywhere else, former revolutionaries are ever only frantically building capitalism.
Violence, then. Of what use is it or has it been, even historically speaking? And what does it mean? Notwithstanding Mao’s ‘political power grows out of the barrel of a gun’ or Sartre’s utterly misplaced idea of violence as a cleansing force: ‘To shoot down a European is to kill two birds with one stone…there remains a dead man and a free man.’ In fact the ‘original’ Indian Maoist – the Naxalite leader Charu Mazumdar was probably closer to this Sartre than either Marx or even Mao. ‘He who has not dipped his hands in the blood of the class enemy is not worthy of being called a communist’ – that was Charu Mazumdar for you. Unlike present day Maoists, of course, Charu Babu, forbade the use of fire-arms. He prescribed smaller everyday arms used by the peasants – the sickle for example – to gruesomely kill and let the blood flow out. Many young followers would then dip their hands in that blood and paint the police stations red. Which Marx or Marxism does this notion of violence come from? It would be difficult, despite Mao’s insistence on the gun, to actually show any such instance in pre-revolution China. Former Naxalite and sociologist Rabindra Ray probably surmised correctly that this kind of ‘cult of violence’ within the early Naxalite movement derived more from Tantrism and the cults of Kali rather than from Marxism – the very indigenous roots of Naxalism, if you please. Some day a more serious investigation of this connection will have to be undertaken and it will also bring out, among other things, the facile and spurious nature of the essentialist notion of a non-violence loving, tolerant India. But that is another story.
In the first decade of the last century, Goerge Sorel responded to a series of debates on violence within the socialist movement in France and Italy. A general disgust with the compromises and betrayal by parliamentary socialist/social democratic parties permeated the militant working class movement. Revolutionary syndicalism was one of the trends that were of vital importance in the Parisian working class and which stood opposed to the idea of ‘state socialism’, advocating rather, a ‘society of associated producers’. Sorel’s tract Reflections on Violence has of course gone down in history as one of the notorious justifications of revolutionary violence but it would be worth looking at one aspect of his reflections which help put things in perspective. For Sorel does not simply justify violence of all sorts. He underlines (borrowing from Kautsky) that ‘the motive force of the revolutionary movement must also be the motive force of the ethic of the producers.’ He interprets this thesis in his own way by arguing that ‘the influence of the syndicates in labour should result from complex and sometimes distant causes, acting on the general character of the workers than from a quasi-military organization.’ In other words, it must be in tune with the life and ethic of the workers/producers – drawing on it as well as acting upon it. In a sense, this is a radical argument against ‘violence as pure means’, insisting that ‘you must be the change that you want the world to be.’ Sorel likens the worker/producer to a soldier of what he calls the ‘wars of Liberty’ – unlike the mercenary soldiers or automatons of royal armies – in that they are already ‘free men’ in spirit.
Sorel finds the same spirit ‘among working class groups who are eager for the general strike’ – ‘they picture the Revolution as an immense uprising which yet may be called individualistic; each working with the greatest possible zeal, each acting on his own account, and not troubling himself much to subordinate his conduct to a great and scientifically combined plan.’ In this release of revolutionary energy by the working class movement, Sorel sees ‘the revolutionary syndicalists’ desire to exalt the individuality of the life of the producer.’ As such, he says, ‘they run counter to the interests of politicians who want to direct the Revolution in such a way as to transmit power to a new minority.’ This appears to be the crux of the matter. Violence – revolutionary violence – can be justified if and only if, it is a mass uprising based on the unleashing of the creative revolutionary energies of the workers/producers; on no account can it be justified from this point of view if it is based on a military or quasi-military organization and led by a minority that will then usurp power ‘on behalf of’ the workers/producers. I hope it is clear by now that this notorious justification of violence by a Marxist-syndicalist is anything but Gandhian. Nonetheless, it is predicated upon a firm and unequivocal rejection of violence perpetrated by a military or a quasi-military clique in the name of the people. Historical experience since Sorel shows clearly how farsighted he (and the early 20th century Syndicalists’) was in claiming that such violence always enables a new minority to usurp power in the name of the people it claims to represent.
Many decades later, in the wake of the May 1968 uprising in Europe, Hannah Arendt revisited the field earlier scanned by Sorel. The new justifications of violence by sections of the New Left led to Arendt’s sustained reflections in her 1969 Essay, also called Reflections on Violence (later followed up by her longer exposition On Violence).
For those who may not be familiar with Arendt’s writings, let us excerpt this passage that situates violence and its place within the Marxist tradition with a fair degree of accuracy:
“The strong Marxist flavor in the rhetoric of the New Left coincides with the steady growth of the entirely non-Marxian conviction, proclaimed by Mao Tsetung, “Power grows out of the barrel of a gun.” To be sure, Marx was aware of the role of violence in history, but this role was to him secondary; not violence but the contradictions inherent in the old society brought about its end. The emergence of a new society was preceded, but not caused, by violent outbreaks, which he likened to the labor pangs that precede, but of course do not cause, the event of organic birth.”
“In the same vein, Marx regarded the state as an instrument of violence at the command of the ruling class; but the actual power of the ruling class did not consist of nor rely on violence. It was defined by the role the ruling class played in society, or more exactly, by its role in the process of production. It has often been noticed, and sometimes deplored, that the revolutionary Left, under the influence of Marx’s teachings, ruled out the use of violent means; the ‘dictatorship of the proletariat’—openly repressive in Marx’s writings—came after the revolution and was meant, like the Roman dictatorship, as a strictly limited period. Political assassination, with the exception of a few acts of individual terror perpetuated by small groups of anarchists, was mostly the prerogative of the Right, while organized armed uprisings remained the specialty of the military.”
Arendt revisits the entire terrain of Marxist and revolutionary engagement with violence and underlines that in the end, all that Sorel eventually did by way of justifying violence was to propose the ‘myth of the general strike’. What was meant to provide the only possible justification of violence in Sorel, turns out in Arendt’s profound reflections, a claim that such a revolutionary mass uprising ceases to be ‘violent’ - for this is precisely the point at which a new power is born.
In fact In the latter part of her essay, Arendt turns to what might be considered one of her most crucial theoretical interventions by proposing a distinction between ‘violence’ and ‘power’. She disaggregates the series of terms often used by political scientists and theorists almost simultaneously – power, violence, force, authority, might and strength. The most critical distinction she makes – and this is of central importance for our discussion – is that ‘Power corresponds to the human ability not just to act but to act in concert. Power is never the property of an individual; it belongs to a group and remains in existence only so long as the group keeps together.’ To quote her further:
‘Power needs no justification as it is inherent in the very existence of political communities; what, however, it does need is legitimacy… Power springs up whenever people get together and act in concert…’
‘Violence needs justification and it can be justifiable, but its justification loses in plausibility the farther away its intended end recedes into the future. No one will question the use of violence in self-defense because the danger is not only clear but present, and the end to justify the means is immediate.’
More importantly: ‘Power and violence are opposites; where the one rules absolutely, the other is absent. Violence appears where power is in jeopardy, but left to its own course its end is the disappearance of power.’
Arendt’s reflections are food for serious thought. For one thing, they draw attention to a very simple but never acknowledged fact: Violence is the symptom of the crisis of power. Put differently, when the figureheads of power lose legitimacy, violence steps in. She gestures to texts by revolutionary theorists (presumably also Engels’ ‘Introduction’ to Class Struggles in France) that talk of the difficulties of armed insurrections in the context of the ‘increased destructive capacities of weapons’ at the disposal of governments. She then proceeds to analyze this proposition. The gap between the state-owned means of violence, she argues, has always been far beyond what people can muster – beer bottles, Molotov cocktails or guns. ‘In a contest of violence against violence the superiority of the government has always been absolute’, she argues. Then what accounts for the success of revolutions? In a move as profound as it is novel, Arendt suggests that ‘this superiority lasts only so long as the power structure of the government is intact – that is so long as commands are obeyed.’
‘When this is no longer the case the situation changes rapidly. Not only is the rebellion not put down, the arms themselves change hands, sometimes within a few hours.’ When commands are no longer obeyed, the means of violence are of no use. This is the next stage of what Lenin called ‘dual power’ – the power of the soviets or counter institutions of popular power standing in opposition to state power. Not all situations of dual power will lead to a dissolution of the old power but when it happens, ‘arms themselves change hands’ and an armed uprising is no longer necessary. This is the secret of the many bloodless revolutions – including the October revolution in Russia. It is also the secret behind the fall of the Soviet empire and the fall of the Berlin wall in more recent times. When an uprising is a truly popular uprising, it has no need for armed combat. Troops themselves change sides. Just as an aside, it is important to underline that the October revolution was a really popular uprising even though the Bolsheviks themselves were a minority in the Soviets. Lenin’s ‘genius’ lay in taking over these institutions of popular power in exactly the way that Sorel feared new minorities would usurp power in the name of the people.
The question of revolutionary violence needs to be seen in this perspective. Violence – the nihilistic violence – undertaken by Maoist armies are undertaken by a handful of quasi-military dalams. Each dalam has not more than ten to fifteen fighters – that is about all. In the best of instances, dalam members constitute no more than a couple of hundred militants. Their support, if and when it exists, is because democratic channels of organizing and fighting are simply not allowed to exist by the short-sighted Indian state and the local vested interests. The Maoist ideologue with whom I began this discussion was betting on his best bet – the Indian state. He and the Indian state are in a permanent compact: each provides the other with its raison d’etre. One need only look at reports produced by Maoist sympathizers – not agents of the state – to be able to see that in regions ‘governed’ by Maoist ‘Sanghams’ (in Chhattisgarh or Gadchiroli, for instance), to see how no dissent or alternative authority is allowed to exist in these areas. What exists is an authoritarian set up where any dissenting person can only meet one fate - death. We can also see in these reports how, not unlike the fascist LTTE in Sri Lanka, families are forced to ‘contribute’ young children to ‘the movement’ (of these reports sound almost apologetic when they narrate such matters).
Critique of this kind of cult of violence is not Gandhian. It can be made from impeccably Marxist positions as well.
Saturday, November 22, 2008
Naxals recruit educated youth to their fold
And when you have both a scholar and a martyr like Com Saketh Rajan ...
What can you expect ?
As of today there are thousands of mini Saketh Rajans in Karnataka
waiting in the wings..
Naxalites in Karnataka recruit educated youth
BANGALORE: A day after killing three Naxalites in an encounter in Chickamagalur, it has now become clear that the Maoist extremists have been attracting the educated youth to propagate and conduct their operations in the jungles of Western Ghats.
The anti-naxal force (ANF) is now concentrating on finding the sympathizers of the extremists' group in and around Chickamagalur and Udupi, two districts located on both sides of the Western Ghats.
Among the three Naxals gunned down by the ANF at Mavianahalla in Chickamagalur, Manohar's name stands apart as he is a graduate and was involved in several progressive movements in his native district of Shimoga. He hails from former chief minister S Bangarappa's home constituency Soraba in Shimoga district.
Manohar was trained under the Maoists at Raichur. He returned to Shimoga and joined a local newspaper as a reporter. He escaped in an earlier encounter with the police while he was in Raicur camp. Later when he was caught, he served a two year jail term and returned to Shimoga, where he joined the newspaper.
He was missing for the last couple of months. Apparently, he had joined his 'comrades' holed up in Western Ghat region coming under Chickamagalur district. His family was scouting for a bride for him,
when he was killed in the encounter in the wee hours of Wednesday.
Devendrappa alias Vishnu was from Soraba Taluk's Tattur village. He was a post-graduate. He also had got involved in several progressive movements in his district of Shimoga along with Manohar. He was also shot dead by the ANF.
The third man, Naveen, who was killed in Wednesday's encounter, was from Mudigere of Chickamagalur. Police have no clue about his background.
DNAThursday, November 20, 2008
Meeting with CRPF Intelligence Officer in Tamil Nadu
Nadu under some very strange circumstances. And he wasn't just
any intelligence officer but claimed to be be involved in countering
Left Wing Extremism.
But before we get to that , I think I should apprise you of some
background details.
It so happens that sometime towards the end of last year,
I took the decision to enroll in a post graduate course.
I wasn't interested in a full time course so after going through
all the Universities that offered distance learning courses zeroed
down on what I thought was the best of the lot which was based
in a city in Tamil Nadu .
The course that I finally chose for various reasons was a masters
in psychology.
Its a 2 year course and all one has to do is write 5 annual exams in a
year and attend 10 days of practicals. So basically I am spared the
torture that most full time students have to endure in the four
walls of a class room.
It is in this psychology practical lab which took place last week in a
city in Tamil Nadu, that I bumped into CRPF
Intelligence officer Pragadeeshwaran G , a tamilian
formerly with the Q Branch of Tamil Nadu but now posted in the
Uttarpradesh - Chhattisgarh Border as an Intelligence Officer in
Counter Insurgency Operations with the CRPF.
Strangely my class had more than a 100 people from diverse
backgrounds and out of the half dozen people or so with
whom I cared to interact with , I happened to meet this officer.
It seems opposites indeed attract..
It seems that he was fresh cadre and had only recently completed
his training and was on study leave from his unit which is currently
posted near the U.P-CG border.. he gave the name of the town
too but it was an unfamiliar term and I seem to have forgotten it.
While some of you may be familiar with the abuses I have hurled
at the CRPF on this blog and even rechristened them as
the Central Rakshas(Demon) Police Force in light of their great
achievements . I do not have anything against them on a personal level.
While for ten days we were in the same practical batch consisting
of 20 members , we hardly spoke again after the first meeting.
I wasn't too enthusiastic about talking to him , while he too
kept to himself.
While I was not able to observe any overt criminal tendencies or mental
illnesses which could have prompted him to enroll in the CRPF , I think
the main reason he could have joined it is for financial reasons.
So this basically classifies him as a mercenary.
While I seem to have finished flirting with the Maoist Movement and
have moved on in life , Pragadeeshwaran G is going to waste his time
engaged in the futile task of countering the Maoist movement.
The same movement which couldn't be finished off by the
combined might of the Indian Army,Police and Paramilitary
forces in the 1970's that too when the naxalite cadre were
armed with pipe guns and fire crackers for self defense.
That now in 2008 when the Maoists have AK-47's and IED's people
indeed believe that the Maoist movement can be countered shows
how cut off the ruling powers in Delhi are from reality.
Wednesday, November 19, 2008
Growing Harrasment and Surveillance of bloggers - A cause for concern
and monitoring of the internet under India's undeclared emergency
will result in serious repercussions in coming days for bloggers
blogging on sensitive political issues has been proved right.
Anti-Raj blog lands north Indian techie in trouble
Beware bloggers. Never vent your fury on the internet, using abusive language. A Kandivili-based electronic and telecommunication engineer, hailing from north India, did just that, and Crime Branch came calling.
Rajat Trivedi (name changed), 27, spewed venom at Maharashtra Navnirman Sena (MNS) chief Raj Thackeray, saying people like him “should be killed”, in a four-page blog - ‘Truth about the Kurla bus encounter’. It also accused Mumbai police of gunning down Patna youth Rahul Raj in a fake encounter aboard a BEST double-decker.
Sleuths of the Cyber Crime Investigation Cell came across the blog on November 6. The internet protocol (IP) address of the user was traced to Thakur Complex in Kandivili (East). Later, sleuths paid Trivedi a visit at his home and recorded his statement.
Asked whether Crime Branch was violating the freedom of speech and expression, guaranteed to people by the Constitution, by monitoring blogs and community websites, Maria said, “A person has the right to state his views on political issues. But, in this case, Trivedi is inciting people to resort to violence. He can’t do that.”
The blogger was forced to delete what he had posted and you can read
his edited post here.
Apparently the Mumbai Cyber Crime Investigation cell wants
bloggers to read their Cyber Laws..
http://www.cybercellmumbai.com/cyber-laws/
Just last week Karnataka Home Minister V S Acharya admitted that the extremists were way ahead of the police both in terms of technology and innovative techniques.
While Mr Yediyurappa the CM of Karnataka stressed on the need for legislation on cyber crime,
Newsarticle
It is not clear as to whom these esteemed and distinguished gentlemen are referring to.. :)
Harassment and surveillance is only going to increase in the coming days..
3 Naxalites and 1 cop killed in Karnataka
Bangalore/Udupi Nov 19: Three naxalites were killed in a fierce encounter with Anti-Naxal Force (ANF) at Mavinahola in Chikmagalur district of Karnataka. Police sources said a police constable of the ANF was also killed during the two-hour gun battle that took place between 1 a.m. and 4 a.m. at Mavina Holla village in Horanadu taluk.
According to police, during a combing operation in the forest, ANF came face to face with four naxals, including a woman. The militants fired at ANF and they returned the fire on the naxal group.



Later, during a search of the area, ANF found three bodies of naxals. While two of them were identified as Manohar and Naveen, the third was yet to be identified. Police constable Guruprasad from Bhagamandala, succumbed to bullet injuries.
Meanwhile in Chikmagalur, inspector general of police A.M. Prasad told reporters that a woman member of the Maoist group had managed to escape under the cover of darkness.
Maoists have a presence in Chikmagalur, a prominent coffee-growing district, and in the coastal districts of Udupi and Dakshina Kannada though there is no estimate of their number.
Tuesday, November 18, 2008
Maoists and SIMI
"It is better to keep your mouth closed and let people think you are a fool than to open it and remove all doubt."
Former SIMI leaders it seems do not believe in this policy..
Interview with Former SIMI President Yasin Patel..
And the Maoist leadership in India wants to build an alliance with these
fools to combat Hindutva Fundamentalism ?
The key to neutralizing Hindutva fundamentalism is divorcing Hindu's from
Hindutva Organisations but this is not easy to do... and definately not
something that the Maoists are capable of...
Fundamentalists thrive on each other and reinforce each other...
That you can finish of one with the help of another is a mistaken point of view.
If current trends continue , I think we will soon witness a mass resurgence of both
Hindutva and Islam inspired fundamentalism both feeding off each other while
the Maoists will find the political space they occupy shrinking.
I would advise the Maoists to stick to exploiting and deepening class differences
rather than taking up religious causes and deepening religious differences.
Maoist's must not forget the political suicide that some Naxalite leaders
committed in West Bengal in the 1970's by their wrong stand on the
Bangladesh War of Liberation.
And in case you still didn't understand what I mean by fundamentalists thrive
on each other you can read the bajrang dal interview.
Bajrang Dal and SIMI are two sides of the same coin..
It would be advisable to maintain equal distance from such organizations.
Friday, November 14, 2008
Documentary on Naxalites , Maoists of Gadhchiroli,Maharashtra - Documentary NewsX
Trailer of the Documentary
Link to video
A very well made documentary despite the many factual errors and biases...
News X is one of the few news channels in the country that is still involved
in reporting news unlike most other news channels who are mainly into
tittytaintment.
A very tragic documentary... especially in the 3rd part towards
the end which showcases the real life tragedy of a naxalite and cop.
Documentary description:
In the Naxal infested district of Gadchiroli, whether it is the naxalite or the policeman who gets killed it is actually the adivasi who gets killed.
Caught in the Crossfire - A documentary on the naxalites/maoists
of Gadhchiroli,Maharashtra.
Part 1
Link
Part 2
Link
Part 3
Link
Thursday, November 13, 2008
Monday, October 20, 2008
Kerala youth get inspired by Naxalite Movement
Thallappavu and Gulmohar are just two of the most recent ones with a naxalite theme..
Com Varghese it seems did not shout his last slogan in vain... almost four decades after
his death "Inquilab Zindabad" is once again reverberating throughout Kerala .
You can know more about these movies in the below posts.
Thallappavu -A Movie on Com Varghese
articles on Com Varghese on this blog
which you can read here , here and here.
Trailor of Thallappavu - English/Malayalam
Link to Video
Review of Movie Thallappavu

Onam comes every year, but “Thalappavu” comes once a decade. There couldn’t be a better Onam gift for Malayalis and Malayalam cinema than “Thalappavu”. Watched the movie today, First day, at SreePadmanabha and I’m still searching for a fault line. This one goes right up there - An All time Classic.
Madhupal makes a dream debut as a director, Prithviraj and Lal give their best performances till date, Babu Janardanan delivers a world class script which will stand its ground in any film festival ,and Azhagappan mesmerises with the Camera. “Thalappavu” is one movie which puts to rest any doubts about the class and scope of malayalam movies. We rank right up there!
“Thalappavu” is a gripping movie, immensely watchable, it doesn’t drag a bit, there is no suspense (starts with the death of the central character), no violence, no comedy, no love lines. Its almost like a Rohinton Mistry novel with tragedy heaped over tragedy, and finally topped with some very sad tragedy. I hate sad movies, and this is not one of them. Its a classic.
In a recent article from the Rupesh Paul-Amal Neerad junta, Rupesh had pointed out that “Story” is not an important part of a movie. While nobody liked his movie, the point remains that, if Cinema is for telling a story then you could as well publish a short story. Making a movie for telling a story is as good as using Google for searching for porn alone, or using your Blackberry for incoming calls alone. Cinema as a medium has immense potential which needs to be tapped. “Thalappavu”, kudos to Madhupal, does exactly that. It uses the medium’s untapped potentials for handing down a classic.
A still from the movie Thallappavu
Story: Thalappavu is a movie about Naxal Varghese who was killed in one of the state’s most controversial police encounters, and P Ramachandran Nair the police constable who shot him (and after 3 decades brought to book his superiors Laxmana and Vijayan who ordered the murder). Lal plays Ravindran Pillai, the constable, who carries with him the burden of the crime for three decades and along the way loses his family, his home and his sanity. Prithvi plays Naxal Joseph and his ghost, which keeps Ravindran Pillai company. The story moves in multi dimension with threads falling in line at their own pace, with every character getting their own space and piece of the tragedy, with recurring and repeating scenes shot from varying perspectives. Dhanya Mary is a find, and she must be here to stay.
Excerpt from the film website,
‘Thalappavu’ (headgear or turban) is a symbol of authority. In many societies, those in the upper social strata wear the turban as a symbol of power and authority. For the working class it provides shade from the hot sun and pelting rain.
The relationship between a hardcore revolutionary and the masses is usually distressing as far as governments are concerned. Everywhere in the world, it is a common practice for the ruling class to fetter one who is ready to sacrifice his life for social causes. The basis of a constitution is that whatever the crime, it is the law of the land that has the right to mete out punishment. The Malayalam movie ‘Thalappavu’ tries to portray that it is the very watchdogs of law who shamelessly violate the rules that they bound to defined.
Good:
1. Script, Screenplay & Direction: “Vasthavam” flopping is one thing I hold against the malayalam audience, then “Thaniyavarthanam” flopped too. Babu Janardanan of “Vasthavam” and “Achanurangatha Veedu”, delivers a water tight script. One can see the effort that has gone into writing this marvel. Madhupal, as a director delivers the script with finesse, but ends up delivering more than the screenplay. It is an exceptional “Director’s movie”, which I guess would catapault Madhupal to Blessy’s seat, now that the latter has started making trash. The story line is spoon fed to the audience multiple times in the first half that we are ready with the details when the movie speeds up in the second half. The delivery is subtle, forceful and passionate. If you look close enough you could even see a Jesus thread hanging around.
Gulmohar - Malayalam movie on Naxalite Maoist Movement in Kerala
Link to video
Review of Malayalam Movie Gulmohar
Once a revolutionary, always a revolutionary' should have been the tagline of Jayaraj's much talked about new Malayalam film Gulmohar. The acting debut of writer-director Ranjith has added to the curiosity value of this endeavour.
Scripted by Didi Damodaran (daughter of T Damodaran, the hit script writer of yesteryears) Gulmohar tells the story of a group of friends who were revolutionaries in their younger days. The tale is told from the point of view of Induchoodan (Ranjith), who now is settled as school teacher with his wife, two kids and mother-in-law.
As Induchoodan jogs down the memory lane, we get glimpse of their adventurous existence mostly lived on the edge as they took on the establishment and fought for the voiceless.
The script as such is packed with lot of layering. The current generation ridicules the suffering and the sacrifices their elders made to make the world a better place. Their relatives never empathised or appreciated the zeal with which they followed their heart's calling or even their sense of justice.
Induchoodan was an orphan (maybe it is used as a tool to justify why he is moved by the plight of others, as conveyed in a scene in the beginning where he tackles a complaint against an orphaned boy in the school) with only an elder sister to call his own. A person with a creative bent of mind, he uses his writing skills to propagate his ideas on revolution.
We fear that Induchoodan's character may go overboard any moment as any conventional multi-talented hero's would. But it is discreetly held back at the script level itself.
The narrative moves from the past to the present, giving us the story of Induchoodan's past and how his present is made.
Ranjith's performance does not look like he was the last minute replacement for the role of Induchoodan (Suresh Gopi [Images] was to play the role). He makes us feel that the part was written with him in the mind. He gives the impression that he has rehearsed well for the part.
Debutant Neenu Mathew is the other performance that impresses us.
Technically too, Gulmohar is in a league of its own, helping Jayaraj to bounce back in form.
Rediff.com
Sunday, October 19, 2008
Ahem...
Read the next post..
A poem by Com Saketh Rajan on the late nigerian journalist,poet and non violent activist Ken Saro Wiwa
Ken Wiwa,poet Playwright, Fist against Shell oil’s might.
Oil of Ogoniland
Oozes and drains
Rows of cocoa, cassava yam.
Slain hero
Okonko’s hoe
Again lies in vain.
From Lagos to London and Holland
Dollars decorate the road
Like a miracle from an oracle’s wand
Pound and Gilder
Girdle Africa’s ankles and hands.
Torso of Ogoniland
Is riddled by the junta
Flames leap up from the rigs
Fly-ash fills the sky.
Ken,
You were killed
On a cloudy night.
Heavy,
The sky
Wept acid-rain
In the streets and the slums
Courtyards of Prisons
A torrent of tears flooded Nigeria’s terrain.
Ken, sorrow of Agonyland.
Niger,
Deep in your delta there’s oil
It boils;
Fresh in your heart there’s blood
It curdles;
Full in your eyes there’s water
It wells.
Nigeria,
Across your beautiful body
Pipelines crisis cross like veins
Blood circulates as oil.
Ken,
You were courageous
Like Okonko
But not keen.
Poet Playwright
Fist against
Hell’s might.
Like the shattered Okonko
You faltered.
Your fist
Was not clenched
In the fight.
Poems and plays–
They’re fine.
They too are weapons
Landmines
In the pathways of the enemy’s mind.
But Abacha
Was a confirmed butcher
Backed by a John Major
And a no-regret Thatcher.
They rule as not by penning sonnets
But by piercing wombs with bayonets.
When they hung Okonko
Perhaps they did not know.
When the Ogonis were shot
It didn’t register a spot.
Anger, you gulped and swallowed
As you walked up the gallows.
But,
It was a lesson
You learned too late.
Your pen
Playwright
Should’ve been backed
By the gun, alright.
Viva Ken,
Poet,
playwright
Wake up
Its past night
Your corpse sleeps in the coffin
Your spirit fills the air.
Stab the heart
That pumps out oil,
Shell the brain
That causes the drain,
Avenge the Saros of humankind.
This poem was written in memory of Ken Saro Wiva, who was a poet playwright and an environmental activist from Nigeria, Africa.
Ken Saro Wiwa(October 10, 1941 – November 10, 1995)

Ken was born in Nigeria in 1941 and he studied in the University of Ibadan. He was hanged by the regime of Nigeria lead by Abacha in the year 1995 (10th of November) though he was not proved guilty of being responsible for the death of four people during the march taken on the eve of world labor day that year.
Ken was an environmental activist who fought for the cause of Ogoni people in Nigeria who were being affected by the multinational Shell Oil Company who had set up their business in Nigeria with the help of the Nigerian regime.
Ken Viva had authored A Forest of Flowers (1987) which was shortlisted for the Commonwealth Writer’s Prize, Sozaboy: A Novel in Rotten English (1985), Basi and Company: A Modern African Folktale (1987) and Prisoner of Jebs (1988). His collection of poems is titled Songs in a Time of War (1985) His play Basi and Company became a long running television comedy series of eighty episodes.
In January 1993 MOSOP(a organisation Ken headed) organized peaceful marches of around 300,000 Ogoni people – more than half of the Ogoni population – through four Ogoni centers, drawing international attention to his people's plight. The same year, Shell ceased operations in the Ogoni region, while the Nigerian government occupied the region militarily.
Saro-Wiwa was arrested again and detained by Nigerian authorities in June 1993, but was released after a month. In May 1994, he was arrested and accused of incitement to murder following the deaths of four Ogoni elders. Saro-Wiwa denied the charges, but was imprisoned for over a year before being found guilty and sentenced to death by a specially convened tribunal, during which nearly all of the defendants' lawyers resigned in protest to the trial's cynical rigging by the Abacha regime.
The resignation of the legal teams left the defendants to their own means against the tribunal, which continued to bring witnesses to testify against Saro-Wiwa and his peers, only for many of these supposed witnesses to later admit they had been bribed by the Nigerian government to support the criminal allegations. The trial was widely criticised by human rights organisations and half a year later, Ken Saro-Wiwa received the Right Livelihood Award for his courage as well as the Goldman Environmental Prize
Very few observers were surprised when the tribunal declared a "guilty" verdict, but most were shocked that the penalty would be death by hanging for all nine defendants. However, many were skeptical that the executions would actually occur, as the Nigerian government would face international outrage and possible sanctions and other legal action should the penalties be carried out.
But on 10 November 1995, Saro-Wiwa and eight other MOSOP leaders (the "Ogoni Nine") were executed by hanging at the hands of military personnel. According to most accounts, Ken was the last person to be hanged and thus forced to watch the death of his colleagues. Information on the circumstances of Saro-Wiwa's own death are unclear, but it is generally agreed that multiple attempts were required before the hanging finally brought Saro-Wiwa to his end.
Via Crazymindseye
Strange..
Both were journalists,writers and took very different paths yet both of them are dead today.
Moral of the Story - ????
Saturday, September 13, 2008
The End

I am done with publishing news and articles about Maoists .
It can get a little monotonous, copy pasting information about
two groups of people who have been killing each other for the last
40 years.
As I have previously mentioned on this blog , I am no Maoist.
I do not agree with their current methods and neither would I recommend
this path to anyone as of now , even though I had different views when I
had started this blog way back in 2006.
I do not want to bore you all with another post as to why I am not a Maoist
for I have made some of the reasons clear in my previous posts.
One of the reasons why I had restarted this blog was to publish
some pending articles which has now been accomplished.
It would be extremely hypocritical on my part to continue
with this pro-maoist blog.
Also there are hundreds of pro-maoist blogs now so the necessity of
this blog has diminished considerably.
The home page of Naxalrevolution shall henceforth carry an index
of important articles which I will compile in the coming days and
there will be no more regular posts.
I thank all bloggers and readers for their co-operation
and encouragement over the last two years.
As for my future course of action, it looks like I am going
to enroll for my masters in one of the social sciences.
In today's world, irrespective of which field one is working in or
studying in, it is imperative to maintain an online presence,
if they wish to be at the cutting edge of their chosen field.
So if I feel the necessity to start another blog , a non political one
I will post about it here.
Regards
Abhay
For Team Naxalrevolution
How to blog anonymously using Wordpress and Tor
Blogger arrests are on the rise all over the world and
India is no exception.
In this changing political scenario bloggers must take adequate precaution
while blogging on sensitive subjects.
The risks involved in non-anonymous blogging has gone up manifold
making the risk - reward ratio extremely unfavorable in my opinion.
While there is nothing we can do about non-anonymous bloggers
who have been blogging for some time now, it is advisable that in
future new bloggers should publish anonymously.
Thanks to the efforts of Global Voices which seeks to build a global anti-censorship network of bloggers and online activists throughout the developing world and is dedicated to protecting freedom of expression and free access to information online we have one of the easiest
guides to online blogging available.
Anonymous blogging cannot get easier than this step by step method.
I wish all future bloggers success in their blogging ventures.
Anonymous Blogging with Wordpress & Tor
Download this guide as a pdf
An early draft of this guide was written by Ethan Zuckerman on April 13, 2005 and updated on October 1, 2006. On August 8, 2007 Global Voices Advocacy published an updated and linkable, blogging-friendly, HTML version of the guide, along with a downloadable PDF file.
Download as PDF File at below link
Anonymous Blogging with Wordpress and Tor

One of the great joys of working on Global Voices has been having the chance to work with people who are expressing themselves despite powerful forces working to keep them silent. I’ve worked with a number of authors who’ve wanted to write about political or personal matters online, but who felt they couldn’t write online unless they could ensure that their writing couldn’t be traced to their identity. These authors include human rights activists in dozens of nations, aid workers in repressive countries as well as whistleblowers within companies and governments.
I wrote a technical guide to anonymous blogging some months back and posted it on Global Voices, outlining several different methods for blogging anonymously. Since then, I’ve led workshops in different corners of the world and have gotten comfortable teaching a particular set of tools - Tor, Wordpress and various free email accounts - which used in combination can provide a very high level of anonymity. The guide that follows below doesn’t offer you any options - it just walks you through one particular solution in detail.
You can feel free to ignore the “why” sections of the guide if you want a quicker read and if you’re the sort of person who doesn’t need to know why to do something. I hope to format this more prettily at some point in the future, allowing the “why” sections to be expanded and compressed, making the whole document a lot shorter.
If I’ve been unclear somewhere in the document or got something wrong, please let me know in the comments - this is a draft which I hope to clean up before posting it on Global Voices. Should you find it useful and want to disseminate it further, feel free - like almost everything on this site, it’s licensed under a Creative Commons 2.5 Attribution license, which means you’re free to print it on coffee cups and sell them, if you think there’s a market and money to be made.
If you follow these directions exactly, you’ll sharply reduce the chances that your identity will be linked to your online writing through technical means - i.e., through a government or law enforcement agency obtaining records from an Internet Service Provider. Unfortunately, I cannot guarantee that they work in all circumstances, including your circumstances, nor can I accept liability, criminal or civil, should use or misuse of these directions get you into legal, civil or personal trouble.
These directions do nothing to prevent you from being linked through other technical means, like keystroke logging (the installation of a program on your computer to record your keystrokes) or traditional surveillance (watching the screen of your computer using a camera or telescope). The truth is, most people get linked to their writing through non-technical means: they write something that leaves clues to their identity, or they share their identity with someone who turns out not to be trustworthy. I can’t help you on those fronts except to tell you to be careful and smart. For a better guide to the “careful and smart” side of things, I recommend EFF’s “How to Blog Safely” guide.
Onto the geekery:
Every computer on the internet has or shares an IP address. These addresses aren’t the same thing as a physical address, but they can lead a smart system administrator to your physical address. In particular, if you work for an ISP, you can often associate an IP address with the phone number that requested that IP at a specific time. So before we do anything anonymous on the Internet, we need to disguise our IP.
What to do if you want to blog from your home or work machine:
a) Install Firefox. Download it at the Mozilla site and install it on the main machine you blog from.
Why?
Internet Explorer has some egregious security holes that can compromise your online security. These holes tend to go unpatched for longer on IE than on other browsers. (Don’t believe me? Ask Bruce Schneier.) It’s the browser most vulnerable to spyware you might inadvertently download from a website. And many of the privacy tools being released are being written specifically to work with Firefox, including Torbutton, which we’ll be using in a future step.
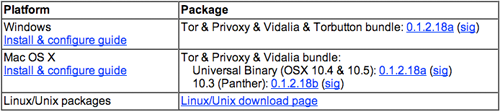
b) Install Tor. Download the program from the Tor site. If access to Tor main website is blocked in your country, there are a few mirrors of it in other places where it can also be downloaded from. Pick the “latest stable release” for your platform and download it onto your desktop. Follow the instructions that are linked to the right of the release you downloaded. You’ll install two software packages and need to make some changes to the settings within your new installation of Firefox.
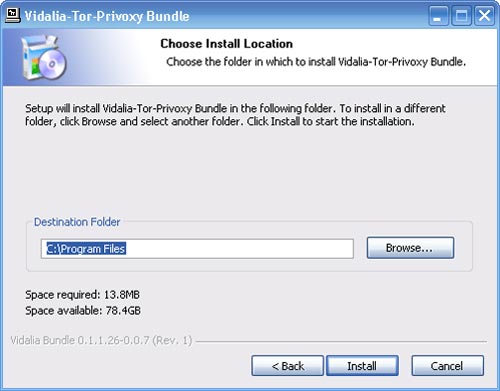
Why?
Tor is a very sophisticated network of proxy servers. Proxy servers request a web page on your behalf, which means that the web server doesn’t see the IP address of the computer requesting the webpage. When you access Tor, you’re using three different proxy servers to retrieve each webpage. The pages are encrypted in transit between servers, and even if one or two of the servers in the chain were compromised, it would be very difficult to see what webapge you were retrieving or posting to.
Tor installs another piece of software, Privoxy, which increases the security settings on your browser, blocking cookies and other pieces of tracking software. Conveniently, it also blocks many ads you encounter on webpages.
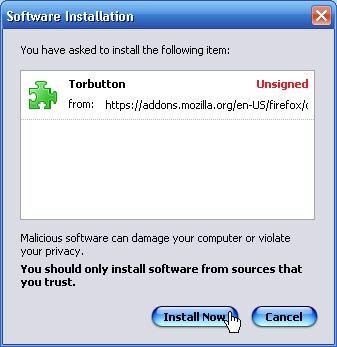
c) Install Torbutton. Read about it and install it, following the instructions on the installation page. You’ll need to be using Firefox to install it easily - from Firefox, it will simply ask you for permission to install itself from the page mentioned above.
Why?
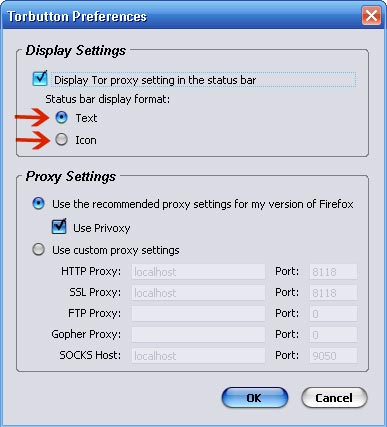
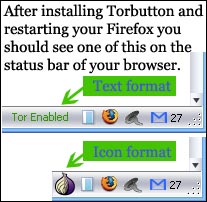
Turning on Tor by hand means remembering to change your browser preferences to use a proxy server. This is a muiltistep process, which people sometimes forget to do. Torbutton makes the process a single mouse click and reminds you whether you’re using Tor or not, which can be very helpful.
You may find that Tor slows down your web use - this is a result of the fact that Tor requests are routed through three proxies before reaching the webserver. Some folks - me included - use Tor only in situations where it’s important to disguise identity and turn it off otherwise - Torbutton makes this very easy.
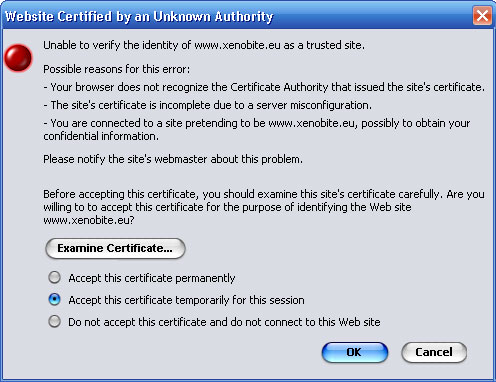
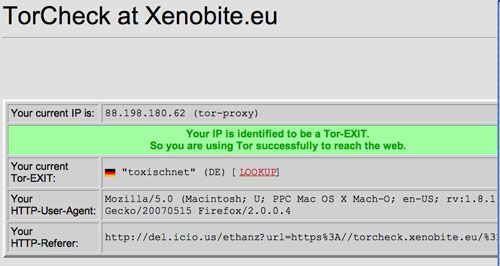
d) Turn on Tor in Firefox and test it out. With Tor turned on, visit this URL (https://torcheck.xenobite.eu/). By clicking, you will get a security alert dialog box - unable to verify the identity of xenobite.eu as a trusted site. Click OK in order to accept the self-signed certificate for that particular session.
After clicking, if you get this message telling you, “Your IP is identified to be a Tor-EXIT. So you are using Tor successfully to reach the web.”, then you’ve got everything installed correctly and you’re ready for the next step.
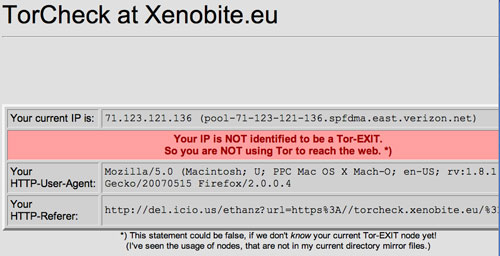
Otherwise you will get this message telling you that “Your IP is NOT identified to be a Tor-EXIT. So you are not using Tor to reach the web”.
Why?
It’s always a good idea to see whether the software you’ve installed works, especially when it’s doing something as important as Tor is. The page you’re accessing is checking to see what IP address your request is coming from. If it’s from a known Tor node, Tor is working correctly and your IP is disguised - if not, something’s wrong and you should try to figure out why Tor isn’t working correctly.
Alternative instructions if you’re going to be writing primarily from shared computers (like cybercafe computers) or you’re unable to install software on a computer.
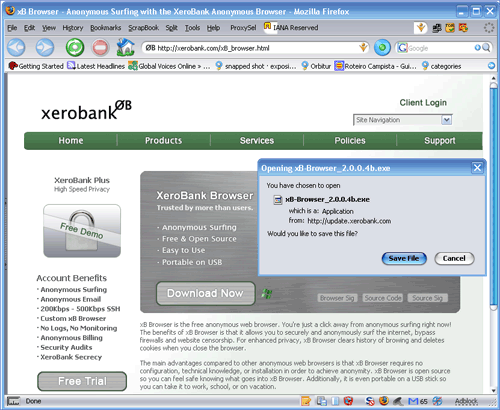
a) Download XeroBank Browser (xB Browser) or alternatively Tor on a Stick (ToaSt). Download the package from the xB Browser site onto a computer where you can save files. Insert your USB key and copy the xB-Browser.exe onto the key. Using this USB key and any Windows computer where you can insert a USB key, you can access a Tor-protected browser. On this shared computer, quit the existing web browser. Insert the key, find the key’s filesystem on the Desktop, and double-click the xB-Browser_latest.exe. This will launch a new browser which accesses the web through Tor.
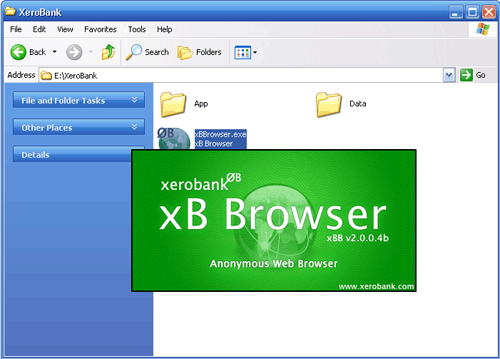
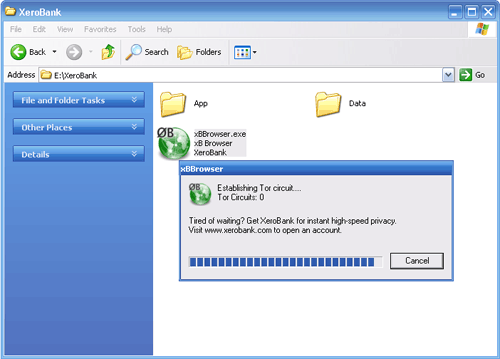
b) Test that XeroBank Browser is working by visiting the Tor test site with the Tor-enabled browser and making sure you get a “Your IP is identified to be a Tor-EXIT” message.
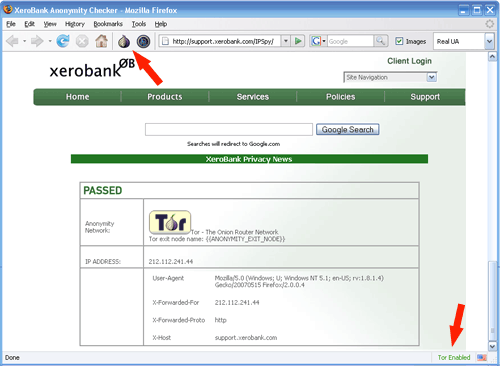
Why?
XeroBank is a highly customized version of the Firefox browser with Tor and Privoxy already installed. It’s designed to be placed on a USB key so that you can access Tor from shared computers that don’t permit you to install software. While I recommend XeroBank and use it when I travel, it is not formally supported by the folks behind Tor - they’re not happy that early versions of the program weren’t released with source code, which meant that it was impossible to determine precisely what XeroBank did and how it used Tor’s source code. A more recent version of the program includes source code - it will be interesting to see whether Tor’s programmers offer their blessing of this version. Roger Dingledine of Tor has also indicated that he and his colleagues are planning an open source version of a portable browser with Tor installed, but the timeline for this new project is unknown.
Step 2: Generate a new, hard to trace email account.
Most web services - including blog hosting services - require an email address so that they communicate with their users. For our purposes, this email address can’t connect to any personally identifiable information, including the IP address we used to sign up for the service. This means we need a new account which we sign up for using Tor, and we need to ensure that none of the data we use - name, address, etc. - can be linked to us. You should NOT use an existing email account - it’s very likely that you signed up for the account from an undisguised IP, and most webmail providers store the IP address you signed up under.
a) Choose a webmail provider - we recommend Hushmail, Vaultletsof and Gmail, but as long as you’re using Tor, you could use Yahoo or Hotmail as well. Also, you can easily register a free and quick webmail account with fastmail.fm.

Why?
Webmail is the best way to create a “disposeable” email address, one you can use to sign up for services and otherwise ignore. But a lot of users also use webmail as their main email as well. If you do this, it’s important to understand some of the strengths and weaknesses of different mail providers.
Hotmail and Yahoo mail both have a “security feature” that makes privacy advocates very unhappy. Both include the IP address of the computer used to send any email. This isn’t relavent when you’re accessing those services through Tor, since the IP address will be a Tor IP address, rather than your IP address. Also, Hotmail and Yahoo don’t offer secure HTTP (https) interfaces to webmail - again, this doesn’t matter so long as you use Tor every time you use these mail services. But many users will want to check their mail in circumstances where they don’t have Tor installed - for your main webmail account, it’s worth choosing a provider that has an https interface to mail.
Hushmail provides webmail with a very high degree of security. They support PGP encryption - which is very useful if you correspond with people who also use PGP. Their interface to webmail uses https and they don’t include the sending IP in outgoing emails. But they’re a for-profit service and they offer only limited services to non-paying users. If you sign up for a free account, you have to log into it every couple of weeks to make sure the system doesn’t delete it. Because they’re aggresive about trying to convert free users to paid users, and because their system uses a lot of Java applets, some find that Hushmail isn’t the right choice for them.
Gmail, while it doesn’t advertise itself as a secure mail service, has some nice security features built in. If you visit this special URL, your entire session with Gmail will be encrypted via https. (I recommend bookmarking that URL and using it for all your Gmail sessions.) Gmail doesn’t include the originating IP in mail headers, and you can add PGP support to Gmail by using the FreeEnigma service, a Firefox extension that adds strong crypto to Gmail (it works with other mail services as well.)
A warning on all webmail accounts - you’re trusting the company that runs the service with all your email. If that company gets hacked, or if they are pressured by other governments to reveal information, they’ve got access to the text of all the mails you’ve received and sent. The only way around this is to write your mails in a text editor, encrypt them on your own machine using PGP and send them to someone also using PGP. This is way beyond the level of secrecy most of us want and need, but it’s important to remember that you’re trusting a company that might or might not have your best interests at heart. Yahoo, in particular, has a nasty habit of turning over information to the Chinese government - Chinese dissidents are now suing the company for illegal release of their data. Just something to think about when you decide who to trust…
b) Turn Tor on in your browser, or start XeroBank. Visit the mail site of your choice and sign up for a new account. Don’t use any personally identifiable information - consider becoming a boringly named individual in a country with a lot of web users, like the US or the UK. Set a good, strong password (at least eight characters, include at least one number or special character) for the account and choose a username similar to what you’re going to name your blog.
c) Make sure you’re able to log onto the mail service and send mail while Tor is enabled. It is most likely that Tor changes its circuit every 10 minutes and this could disrupt your webmail operations, so you should consider limiting the process of writing a new email to 10 minutes.
Step 3: Register your new anonymous blog
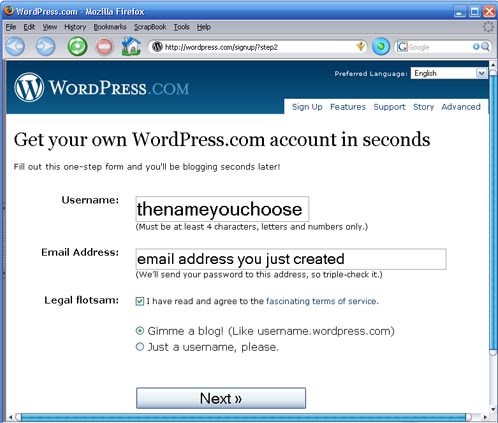
a) Turn Tor on in your browser, or start XeroBank. Visit Wordpress.com and sign up for a new account by clicking the “Get a New WordPress Blog” link. Use the email address you just created and create a username that will be part of your blog address: thenameyouchoose.wordpress.com
b) Wordpress will send an activation link to your webmail account. Use your Tor-enabled browser to retrieve the mail and follow that activation link. This lets Wordpress know you’ve used a live email account and that they can reach you with updates to their service - as a result, they’ll make your blog publicly viewable and send you your password. You’ll need to check your webmail again to retrieve this password.
c) Still using Tor, log into your new blog using your username and password. Click on “My Dashboard”, then on “Update your profile or change your password.” Change your password to a strong password that you can remember. Feel free to add information to your profile as well… just make sure none of that information is linked to you!
a) Write your blog post offline. Not only is this a good way to keep from losing a post if your browser crashes or your net connection goes down, it means you can compose your posts somewhere more private than a cybercafe. A simple editor, like Wordpad for Windows, is usually the best to use. Save your posts as text files (After blogging, always remember to remove these files from your machine completely, using a tool like Eraser or Ccleaner which is is available in many languages and wipes temporary files automatically from all installed browsers and other applications).
).
b) Turn on Tor, or use XeroBank, and log onto Wordpress.com. Click the “write” button to write a new post. Cut and paste the post from your text file to the post window. Give the post a title and put it into whatever categories you want to use.
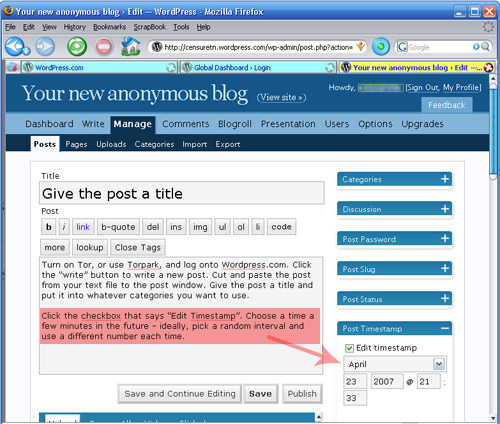
c) Before you hit “Publish”, there’s one key step. Click on the blue bar on the right of the screen that says “Post Timestamp.” Click the checkbox that says “Edit Timestamp”. Choose a time a few minutes in the future - ideally, pick a random interval and use a different number each time. This will put a variable delay on the time your post will actually appear on the site - Wordpress won’t put the post up until it reaches the time you’ve specified.
Why?
By editing the timestamp, we’re protecting against a technique someone might use to try to determine your identity. Imagine you’re writing a blog called “Down with Ethiopia Telecommunications Company!” Someone at ETC might start following that blog closely and wonder whether one of their customers was writing the blog. They start recording the times a post was made on downwithetc.wordpress.com and check these timestamps against their logs. They discover that a few seconds before each post was made over the series of a month, one of their customers was accessing one or another Tor node. They conclude that their user is using Tor to post to the blog and turn this information over to the police.
By changing the timestamp of the posts, we make this attack more difficult for the internet service provider. Now they’d need access to the logs of the Wordpress server as well, which are much harder to get than their own logs. It’s a very easy step to take that increases your security.
a) Securely erase the rough drafts of the post you made from your laptop or home machine. If you used a USB key to bring the post to the cybercafe, you’ll need to erase that, too. It’s not sufficient to move the file to the trash and empty the trash - you need to use a secure erasing tool like Eraser or Ccleaner which overwrites the old file with data that makes it impossible to retrieve. On a Macintosh, this functionality is built it - bring a file to the trash and choose “Secure Empty Trash” from the Finder Menu.
b) Clear your browser history, cookies and passwords from Firefox. Under the Tools menu, select “Clear Private Data”. Check all the checkboxes and hit “okay”. You might want to set up Firefox so that it automatically clears your data when you quit - you can do this under “Firefox -> Preferences -> Privacy -> Settings”. Choose the checkbox that says “Clear private data when closing Firefox”. In case you cannot install programs on the computer, use the IE Privacy Cleaner tool from the USB stick to wipe temp browser data.
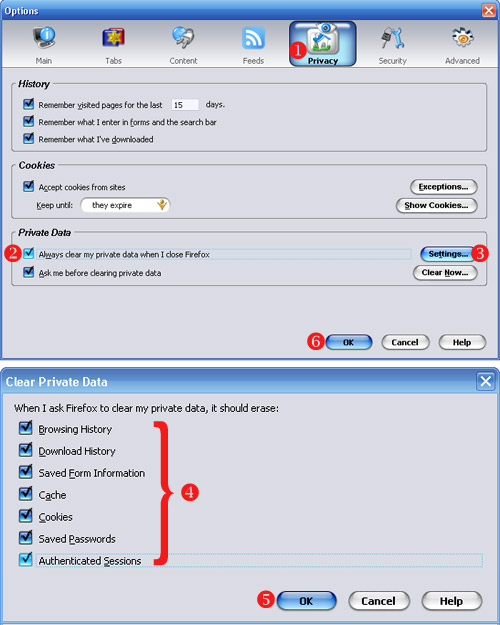
Why?
It’s very easy for someone to view the websites you’ve visited on a computer by reviewing your browser history. More sophisticated snoops can find out your browsing history by checking your cache files, which include stored versions of webpages. We want to clear all this data out from a public computer so that the next user doesn’t find it. And we want to eliminate it from our personal computer so that if that computer were lost, stolen or seized, we can’t be linked to the posts we’ve made.
- It’s not enough just to protect yourself when writing to your own blog. If you’re going to post comments on other blogs using your “nom de blog”, you need to use Tor when posting those comments as well. Most blog software records the IP a comment came from - if you don’t use Tor, you invite whoever runs that site to track your IP address back to your computer. Tor’s like a condom - don’t practice unsafe blogging.
- Just because you’re anonymous doesn’t mean you shouldn’t make your blog pretty. The “Presentation” tab in Wordpress has lots of options to play with - you can pick different templates, even upload photos to customize some of them. But be very, very careful in using your own photos - you give a lot of information about yourself in posting a photo (if the photo was taken in Zambia, for instance, it’s evidence that you are or were in Zambia.)
- If you’re really worried about your security, you might want to go a step further in setting up your Firefox browser and turn off Java. There’s a nasty security bug in the most recent release of Java that allows a malicious script author to figure out what IP address your computer has been assigned EVEN IF YOU ARE USING TOR. We don’t worry too much about this because we don’t think that Wordpress.com or Google are running these malicious scripts… but it’s something to seriously consider if you’re using Tor for other reasons. To turn off Java, go to “Firefox -> Preferences -> Content” and uncheck the box for Enable Java.
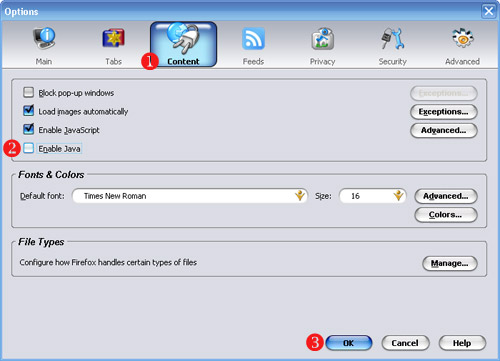
- If you’re the only person in your country using Tor, it becomes pretty obvious - the same user is the only one who accesses the IP addresses associated with Tor nodes. If you’re going to use Tor and you’re worried that an ISP might be investigating Tor use, you might want to encourage other friends to use Tor - this creates what cryptographers call “cover traffic”. You also might want to use Tor to read various websites, not just to post to your blog. In both cases, this means that Tor is being used for reasons other than just posting to your anonymous blog, which means that a user accessing Tor in an ISP’s server logs doesn’t automatically make the ISP think something bad is taking place.
A final thought on anonymity: If you don’t really need to be anonymous, don’t be. If your name is associated with your words, people are likely to take your words seriously. But some people are going to need to be anonymous, and that’s why this guide exists. Just please don’t use these techniques unless you really need to.
Index of steps involved
Introduction
Disclaimer
Step 1: Disguise your IP
a) Install Firefox.
b) Install Tor.
c) Install Torbutton.
d) Turn on Tor in Firefox and test it out.
Alternative instructions
a) Download XeroBank Browser (xB Browser)
b) Test that XeroBank Browser is working
Step 2: Generate a new, hard to trace email account.
a) Choose a webmail provider.
b) Turn Tor on in your browser, or start XeroBank.
c) Make sure you’re able to log onto the mail service.
Step 3: Register your new anonymous blog.
a) Turn Tor on in your browser.
b) Wordpress activation link.
Log into your new blog.
Step 4: Post to your blog.
a) Write your blog post offline.
b) Log onto Wordpress.com.
Edit Timestamp.
Step 5: Cover your tracks
a) Securely erase the rough drafts
b) Clear your browser history, cookies and passwords from Firefox.
Some parting thoughts.
A final thought on anonymity.
Show your support!





